|
|
Application Note 1008Using the IPNetSentry Bandwidth Analyzer (IBA) as an IP Security Analysis Tool
|
Scenarios 1. Your Mac OS X system is up and running, but you are not currently doing anything with it. You look over to your cable (or DSL) modem to see the activity light occasionally flashing. You wonder "what is going on here"? 2. You've heard a lot in the news lately about "worms" being released and how they may slowdown the Internet. You wonder if your machine, even if it is a Macintosh, is being subjected to any of this activity. Step 1: Acquire Data We first need to acquire bandwidth and security log data using IPNetSentryX. The easiest way to acquire this data is to download and install the Bandwidth Analyzer application (available from our Downloads page). In this package you will find an IPNetSentryX document entitiled "Bandwidth Accounting". Open this document to install the needed filters. The needed filters are simply a collection of logging filters that start with the underscore character "_". Such filters cause matching datagrams to be logged in a daily Bandwidth Logging file. You can view the specific Bandwidth Logging filters by opening the 1.5 and 1.6 rules set. This document will also enable logging of all incoming and outgoing datagrams in a daily Security Log file. In addition to opening this document you must also open the IPNetSentryX Preferences window and:
Once these settings have been made, let IPNetSentryX acquire a few hours worth of data. You can be using the machine at the time or just let it sit idle (but it should not go to sleep). Step 2: Analyze Data Now that we have some data to analyze, we can launch the IPNetSentryX Bandwidth Analyzer. Open the recently created "bandwidth log YYYY-MM-DD.plist" file. Depending on how much data has been acquired, this may take a few moments as the Bandwidth Analyzer parses this file. Once loaded, you can simply plot all the data in the list by clicking the "Graph All" button. This should create a plot similar to the following:
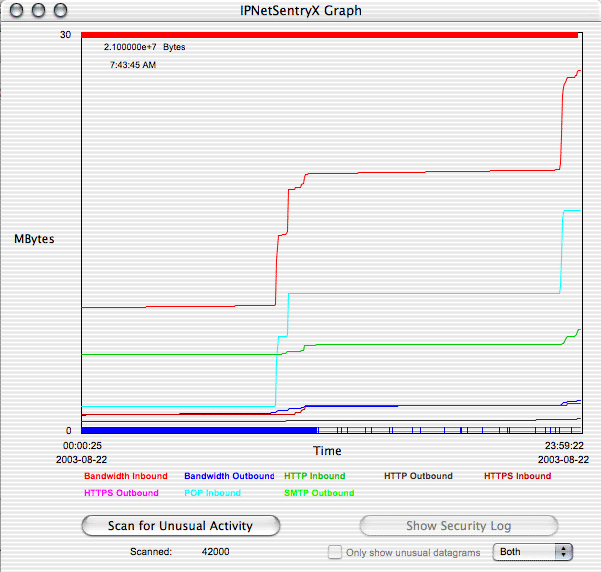
Now click the "Scan for Unusual Activity" button. This action may take some time (please be patient). The Bandwidth Analzyer is examining every datagram received by or sent from your machine, and seeing if the datagram is "unexpected" behavoir. Unexpected datagrams are marked by small red (incoming) or blue (outgoing) tick marks at the top and bottom of the plot, respectively. If you have a lot of unexpected activity, the ticks may actually appear as a solid 5 pixel high lines at the top and bottom of the plot. Here is the result of our unusual activity security scan:
Note the solid red and blue "lines" at the top and bottom of the plot. The blue line only extends to about 11:30 AM, afterwhich we invoked a special filter, but more on this later. This clearly shows us that our machine is being subjected to plenty of unexpected incoming and outgoing activity. To see exactly what is happening. click in the plot region itself and drag to the right in order to select a region of the plot for more detailed Security Log analysis:
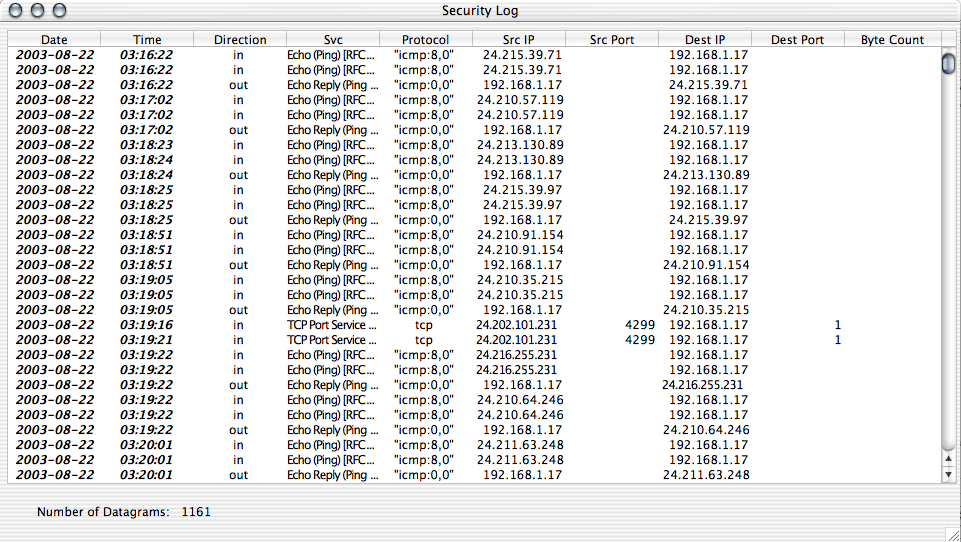
This will enable the "Show Security Log" button. Click the "Only show unusual datagrams button, and leave the popup menu set at "Both" (we want to examine both incoming and outgoing datagrams). Click the "Show Security Log" button. Once again, because we are looking at every datagram passed to and from the machine, this process may take a few moments. Once completed, you should see a list similar to the following (your list, however,will depend on the specific unusual activity of your network connection):
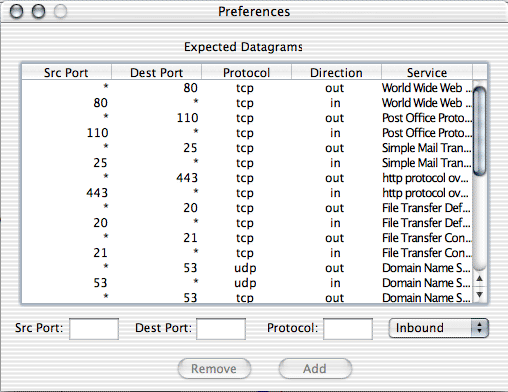
This data immediately shows us that our machine is being subjected to numerous ICMP Pings. In this case, this is due to a recent release of a Windows worm (W32.Welchia.Worm). Step 3: Add Additional Filters Now that we know the source of most of our "unusual" Internet activity, we are in a position to address it. In this case the solution is relatively simple: add a trigger for any incoming ICMP Ping datagrams. Having done this at about 11:30 A.M, we see that our unusual outgoing activity was significantly stopped (this ICMP Ping trigger is actually part of the Bandwidth Accounting rules set, specifically rule 2.4.1.3.3). Note that we cannot stop the initial incoming ICMP Ping datagram, since these are directly being delivered to us by our ISP (who does not know if this is a legitimate or illegitimate datagram). The importance of stopping the Ping reply from our machine should be highlighted. This is because: - by stopping the reply, the remote infected machine (probably a Windows machine) will not even know our machine is on the Internet, hence will normally stop transmitting datagrams to this "inactive" IP address. - by stopping the reply we save precious upstream bandwidth. Normally all cable and DSL (ADSL) connections are highly asymmetric. We are given far more downstream bandwidth than we are given upstream bandwidth. IF we continue to reply to unwanted Ping Echo requests, we are only wasting our upstream bandwidth which could be better used for our wanted connections to remote locations. We then repeat Steps 2 and 3 as needed to identify and block other unwanted and unusual activity. Definition of "Unusual Activity" When performing the Unusual Activity scan, the Bandwidth Analyzer compares each incoming and outgoing datagram to a list of expected services. This list of expected services can be viewed and edited through the Bandwidth Analyzer Preferences window:
The default list should be good for most users who are using their machines for standard Internet activities such as web browsing, file downloading, and email. Add or remove services (ports and protocols) as needed for your specific Internet activities. A current and complete list of standard Internet services can be found at: http://www.iana.org/assignments/port-numbers Conclusion Packet security analysis use to be the domain of large corporate network administrators. With the recent release of several worms to the Internet at large, it can be beneficial to each of us to occasionally perform our own security analysis. Not only such analyses point out general deficencies in our firewall policies (rules), but subsequent actions might also help increase the overall performance of our network connections. The IPNetSentryX Bandwidth Analyzer is one tool which will signficantly aid the lay person in performing these security audits. Please send questions, comments, or suggestions using our general
requests form: |
|
 Privacy
Policy
Privacy
Policy  Contact
Us
Contact
Us